
All new technologies strive to ease the burden of complex business problems which is why you need to start looking at how big data analysis helps your compliance efforts. Increasingly, cyber security compliance requires companies to analyze the impact of diverse information inputs and streams. Thus, big data analytics provide important compliance insights that enable your organization to streamline it efforts and increase profitability.
Using Big Data to Drive Your Business & Compliance Program
What is Big Data?
All over the internet, technology professionals throw around the term “big data.” Big data means large sets of information that computers can analyze mathematically to show patterns, trends, and associations. However, this definition doesn’t address what big data really is.
Traditionally, big data incorporates the three V’s of volume, velocity, and variety. Volume means not just the amount of data but the number of places from which you collect data. For example, information comes from business transactions, social media, or sensors to help find patterns. Velocity incorporates the speed of collection to ensure timely review. For example, sensors and RFID tags allow you to collect information in real-time so you can see what’s happening as soon as possible. Finally, variety means the data’s format. Information can be numeric, text-based, visual, audio, structured, or unstructured.
What is the “variability” problem?
Variability means that data can change over the course of processing. While the term is related to variety, it’s also different. Variety incorporates the sources of data which provide different types of information such as images and text. Meanwhile, variability talks about inconsistencies in the data arising out of the disparate types and sources.
For example, the data point “ocean” can be:
- Text:
- Atlantic
- saltwater
- waves
- Pacific
- Image:


Collecting data about the ocean would bring text as well as images (and video, audio, and others). The text “wave” might mean moving a hand in greeting or it might mean the way water approaches a shore. When textual data is aggregated, the hand gesture will be an outlier even though it might be in the collected information.
Meanwhile, the images for “wave” would more likely be related to the same definition. However, the way in which they present are different, as in the above example,
These differences, or variabilities, often make aggregating the variety of data to find similarities difficult. The greater the variability, the greater the complexity. Since the images may represent “wave” in more ways than the text does, the images contain greater complexity.
The complexity that lives in the variability makes analysis of all these different data types difficult.
What are structured and unstructured data?
The primary computational problems with big data lie in the difference between structured and unstructured data.
Structured Data
Structured data incorporates information easily displayed in tables for easy ordering and processing. Think, in this case, of a spreadsheet. You can manipulate the columns to create a variety of views into the data.
Unstructured Data
Most information collected, however, is not in easily organizable tables. Unstructured data traditionally includes text, images, or binary programming that makes numerical organizing difficult.
Sometimes the data collected is a combination of both structured and unstructured. Emails, for example, have structured information that fit in “tables” such as the to, from, and subject lines. However, the text in the message is unstructured.
For example, you can turn the unstructured text data above and make it structured data:
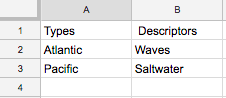
However, the images above do not translate as easily into a structured table.
How do you analyze big data?
Protecting your data environment requires the volume, velocity, and variety that big data brings. More information stored in more locations using more vendors increases the number of attack vectors. The increase in landscape makes protecting it more difficult. Moreover, malicious attacker methodologies continuously evolve thus requiring you to have insights that match their speed. Big data collects the information. However, analytics give you the insights necessary to enable better business decisions.
Predictive Analytics
Predictive analytics uses modeling, machine learning, and data mining to use historical data to predict future events. These statistical modeling methodologies allow you to use the overwhelming real-time data collection effectively. For example, cutting-edge anti-virus protection uses machine learning and big data to predict the next ransomware attacks rather than only protecting against already known ransomware.
Prescriptive Analytics
Prescriptive analytics takes data and helps model best decisions. Rather than simply taking a guess at what might happen to your organization like predictive analytics, the prescriptive analytics model enables you to take actions that can protect your organizations. For example, big data can collect information about attempted intrusions and then the prescriptive analytics models can help you decide which ones to prioritize.
How you can enable information security with big data and machine learning analytics
Once you collect all the data, you need to use the statistical methodologies to make that information useful. Bringing together predictive and prescriptive analytics, you can use the collected big data to protect your environment and monitor control effectiveness. For example, new technologies, like security ratings, continuously collect, aggregate and analyze publicly available data to enable insight into your control effectiveness and that of your vendors.
The machine learning algorithms used for threat detection take information from all across the internet and combine it together. While you may be monitoring your environment yourself, these big data analytics solutions compare millions upon millions of monitored environments against one another to determine normal versus abnormal network and system activities. By aggregating all of this information, these solutions show you attacks against other environments to help you prepare and protect against something that has not yet happened to you.
How big data and machine learning enable compliance and better business decisions
Starting with a strong security stance allows you to build a strong compliance program. With the idea of a “Security First” approach to compliance, you can focus your program to align across multiple frameworks. Determining your control effectiveness as part of your governance program allows you to ensure ongoing compliance. For example, a primary compliance directive across standards and regulations includes ensuring that you patch systems and networks with the most recent software updates. If your continuous monitoring analytics show a weakness in your software updates, then you can better prove compliance.
How ZenGRC Works Similar to Big Data Analytics
With ZenGRC’s System of Record, you can aggregate your compliance documentation and align it across multiple standards to enable better compliance insights.
Dashboards help you track the completion status of your InfoSec compliance programs, and prioritize your efforts when new requirements or frameworks are added. Just as big data collects information across the internet, ZenGRC collects information across your enterprise. In the way that big data predictive analytics can enable better macro insights, ZenGRC enables better organizational insights.
With ZenGRC you can easily leverage work across compliance initiatives, test controls once and use evidence multiple times. You can also run audits and automate routine compliance tasks using ZenGRC. The same way that big data collection finds patterns across information on the internet, ZenGRC enables pattern finding within your compliance program to make the process more efficient.
To schedule a demo, contact ZenGRC today.
