NIST 800-53 and FedRAMP act as the peanut butter and jelly of governmental compliance fundamentals. While NIST 800-53 sets out prescriptive controls for data integrity, FedRAMP offers the complimentary controls for cloud service providers (CSP). This means that for any organization trying to be fully compliant for government work, understanding how NIST 800-53 and FedRAMP are integrated is an important part of the compliance stance.
Why Do I Care About NIST 800-53?
If you plan to work with government agencies, you should care about NIST 800-53. The Federal Information Security Act of 2002 (FISMA) requires agencies to develop, document, and implement programs to protect information. FISMA not only applies to agency assets, but also to those provided or managed by another agency, contractor, or other source.
In other words, that awesome government contract you want? Chances are it’s going to require FISMA compliance.
NIST 800-53 offers prescriptive requirements to help you meet these compliance needs. This is distinct from using the NIST Cybersecurity Framework as your compliance foundation.
What Does NIST 800-53 Require?
NIST 800-53 offers guidance for creating privacy and security policies and controls. At the highest level, the standard gives you a road map for creating IT asset assessments based on risk tolerance.
In building an effective assessment plan, NIST 800-53 defines ten specific key activities. At the most basic level, they want you to create policies, establish oversight, ensure communication, define controls, create time frames, select audit/assessor teams, and store documentation.
This is one of the places where GRC automation is most effective. When you break down communication silos, you more easily share information and documentation between internal stakeholders. In addition, when you have a single location for storing documentation of your controls and policies, your oversight requirement is easier.
Where Does FedRAMP Fit In?
FedRAMP helps you implement the NIST 800-53 in relation to cloud service providers (CSP). NIST 800-53 requires your organization to take into account system/platform and organization-related considerations.
Often, organizations hire third party service providers, such as CSPs. This means that you may not have direct control over the security or privacy controls used in those external systems, and you have to review them differently. Under “3.2.3 Tailor assessment procedures”, NIST 800-53 allows you to tailor the assessment procedures listed in Appendices F and J to meet these kinds of needs.
When tailoring your review, you can use FedRAMP to meet those goals.
What are FedRAMP’s three main principles?
FedRAMP focuses on creating a risk tolerance model to review your CSP’s ability to keep information secure. The three tenets of managing information systems are reviewing confidentiality, integrity, and availability of data transmitted, processed, or stored by the information system.
FedRAMP offers you a way to focus your CSP risk within the boundaries of the NIST 800-53. For example, FedRAMP lists three risk levels: low, medium, and high.
These levels are based on how a security compromise would impact business activities, damage assets, and result in financial loss and harm to others. For example, a low risk associated with a cybersecurity event might involve access to a draft of this blog post as part of an event that compromises a Google Drive account that only contains random blog post drafts. The worst that can happen is erasure of a few hours of work. A medium risk might involve an attack on the WordPress hosting site, in which a year’s worth of posts get changed to the wrong information but no identifying user data gets compromised. A high risk event might be taking down the entire corporate site for several days.
As you think about your risk levels for all of your different assets, remember that different business areas may have different risks.
How do you use FedRAMP to determine risk?
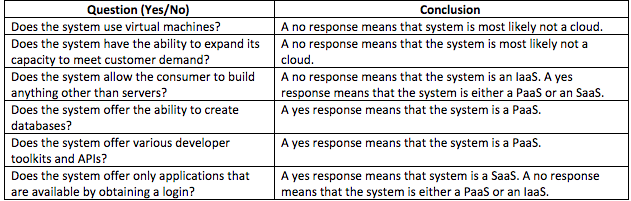
FedRAMP has a two step process to determine the risk. First you need to determine what type of service provider you have. To do this, FedRAMP offers the following chart:
Platform as a Service (PaaS) and Software as a Service (SaaS) are considered “major applications,” so they require a higher level of scrutiny. Meanwhile, Infrastructure as a Service (IaaS) is a “general support system.” When you apply this determination within your NIST Target Profile, think about your reliance on the CSP. If you heavily rely on your CSP for daily business activities, your risk is highly integrated with that of your CSP.
Let’s go back to the example above. Blog content can easily be replicated, though the information is valuable in terms of time spent researching and writing. If the CSP has a cyber event, there will be an inconvenience, but little harm is done. However, if consumer data is located in that cloud drive as well, then the risk is higher for everyone.
In addition, FedRAMP provides ways to review the risk associated with the deployment of the services. These can be public, private, for government community only, or hybrid. By understanding your CSP’s audience, you can understand their approach to security as well.
How to automate NIST 800-53 and FedRAMP for successful FISMA compliance
When reviewing CSPs, controlling user access is the first line of defense. This means that you need to constantly monitor who has access to what systems.
When you automate NIST 800-53 and FedRAMP to meet FISMA compliance requirements, you create a smoother process to keep these authorizations updated. With a larger organization, keeping track of the different individuals who have access becomes more complicated. Having a single location where all the user authorizations are documented makes it easier to incorporate the appropriate oversight.
In addition, since the authorizations listed in your FedRAMP analysis will likely overlap with your NIST analysis, automating the documentation process not only saves time but keeps information consistent.
Incorporating a CSP into your business activities means adjusting your NIST 800-53 evaluation. In doing this, you will need more documentation to satisfy requirements. By using an automated GRC tool, you can strengthen your compliance stance more easily. When you automate NIST 800-53 and FedRAMP for successful FISMA compliance, the end results are better audit outcomes and greater client confidence.
To better understand how ZenGRC automation can help you navigate your FedRAMP and NIST risk, read our eBook Compliance Management Best Practices: When Will Excel Crush You?